Evercookies, Secrets and Fingerprints – 2016
What are Evercookies
Supercookies and evercookies are the result of a website owner’s desire (or more often, that of the advertising networks) to accumulate data about computer users and the sites that they visit, even those users that disable or clear cookies in their browser regularly. Even in “Incognito Mode” that should block cookies, many techniques persist to track your digital browser fingerprint.
Intro
Worldwide, the number of people and the time spent browsing the web keeps increasing. Accordingly, the technologies to enrich the user experience are evolving at an amazing pace. Many of these evolutions provide for a more interactive web (e.g., boom of JavaScript libraries, weekly innovations in HTML5), a more available web (e.g., explosion of mobile devices), a more secure web (e.g., Flash is disappearing, NPAPI plugins are being deprecated), and a more private web (e.g., increased legislation against cookies, huge success of extensions such as Ghostery and AdBlock). Nevertheless, modern browser technologies, which provide the beauty and power of the web, also provide a darker side, a rich ecosystem of exploitable data that can be used to build unique browser fingerprints.
What
Browser fingerprinting consists in collecting data regarding the configuration of a user’s browser and system when this user visits a website. This process can reveal a surprising amount of information about a user’s software and hardware environment, and can ultimately be used to construct a unique identifier, called a browser fingerprint. The privacy implications are important because these fingerprints can then be used to track users. This threat to privacy is extremely serious as assessed by recent studies show the wide adoption of browser fingerprinting.
Meanwhile, large companies such as Google implicitly announce its adoption (e.g., Google’s privacy policy update of June 2015 indicates that they use “technologies to identify your browser or device” [3], which can be interpreted as the inclusion of browser fingerprinting in their identification technologies).
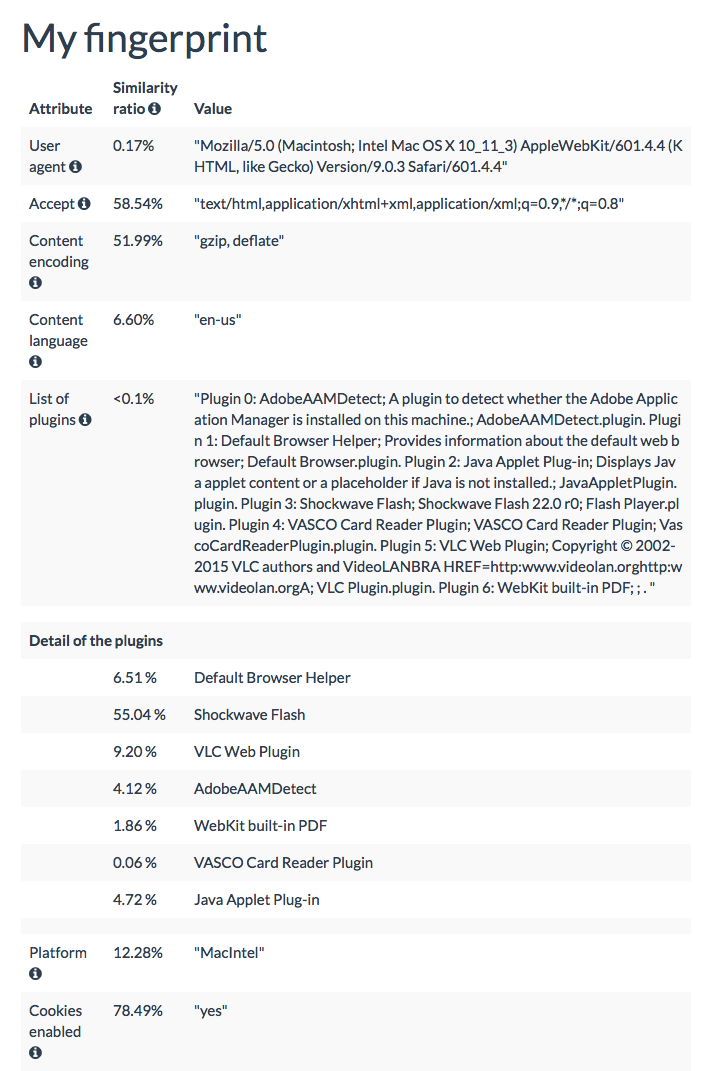
- the User agent header
- the Accept header
- the Connection header
- the Encoding header
- the Language header
- the list of plugins
- the platformBrowser
- the cookies preferences
- the Do Not Track preferences
- the timezone
- the screen resolution and its color depth
- the use of local storage
- the use of session storage
- a picture rendered with the HTML Canvas element
- a picture rendered with WebGLRendering
- the presence of AdBlock
- the list of fontsFlash
In addition to these data, we collect several kinds of housekeeping information to assist us in analyzing the fingerprint data. The housekeeping information is:
- Cookies
- Encrypted IP addresses
- Timestamps
The Artwork
De Wilde collaborated with computer scientist Benoit Baudry to develop raw data output which the artist translated in a 3d environment. The sculpture is based on the browser data from the artist by applying a 17-attribute fingerprinting script that uses modern web technologies developed by INSA-Rennes, University of Lille and INRIA. More info here: https://amiunique.org
Example: Here are my browser fingerprinting stats for my instance of Firefox along with Chrome with and without the Flash plug-in enabled.
- Firefox (my main browser, which I don’t use for BP):
- User_agent: 8.39
- HTTP_ACCEPT Headers: 3.61
- Browser Plugin Details: 22.35+
- Time Zone: 3.69
- Screen Size and Color Depth: 3.72
- System Fonts: 21.35
- Are Cookies Enabled?: 0.43
- Limited supercookie test: 0.86
- Chrome (close-to-clean install, what I normally use to run BP with little to no issues):
- User_agent: 11.29
- HTTP_ACCEPT Headers: 6.59
- Browser Plugin Details: 8.61
- Time Zone: 3.69
- Screen Size and Color Depth: 3.72
- System Fonts: 21.35
- Are Cookies Enabled?: 0.43
- Limited supercookie test: 0.86
- Chrome (optimized? version):
- User_agent: 11.29
- HTTP_ACCEPT Headers: 6.59
- Browser Plugin Details:
16.598.613.49 (see update 2) - Time Zone: 3.69
- Screen Size and Color Depth: 3.72
- System Fonts: 2.31
- Are Cookies Enabled?: 0.43
- Limited supercookie test: 0.86
- Using the UA string and the HTTP_ACCEPT header
- User_agent: 8.39
- HTTP_ACCEPT Headers: 3.61
- Browser Plugin Details:
16.598.613.49 (see update 2) - Time Zone: 3.69
- Screen Size and Color Depth: 3.72
- System Fonts: 2.31
- Are Cookies Enabled?: 0.43
- Limited supercookie test: 0.86